Defend
Threat Detection
& Hunting
Always one step ahead of attackers: Reliable detection of complex attacks across your entire IT infrastructure and actionable remediation advice
![]()
Maximum security
Not all threats are created equal. Our managed security service helps you differentiate and prioritize in order to promptly respond to threats.
![]()
24/7 monitoring
Thanks to reliable round-the-clock monitoring of your systems, you will be informed about critical alerts at any time.
![]()
Efficient threat prevention
If suspicious behavior is detected, we will take action and isolate the affected devices or block compromised accounts.
360° overview across all domains
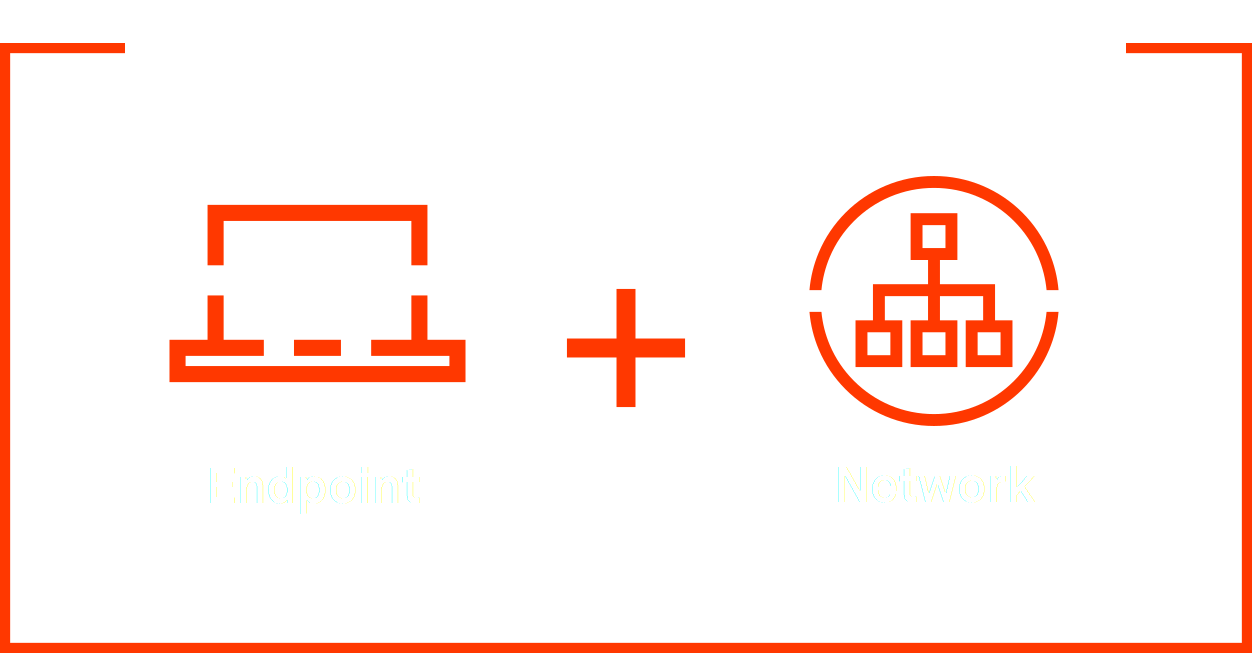
Attacks can originate from a wide variety of sources inside or outside your company. This is why the detection of complex attacks requires a comprehensive overview across all domains of your IT infrastructure.
Although endpoints are constantly the target of attacks, they are often circumvented by attackers. Therefore, detection in network traffic is equally important.
Our all-in-one solution TDH Complete correlates endpoint and network data as well as additional contextual information for maximum visibility and efficient threat prevention. If suspicious behavior is detected, we will take action and, for instance, isolate the affected devices or block compromised accounts – this way, threats can proactively be prevented.
You can find all details on our service in the free data sheet.

Cutting-edge network sensor technology
Our high-performance sensors monitor your traffic and seek threat indicators which are constantly updated. In addition to commercial and freely available sources, we use our own threat intelligence as well as insights from our DCSO community to provide comprehensive visibility of your traffic. With our managed security service, your threat defense is automatically up to date at all times.
Thanks to our exclusive network, we have access to the latest threat intelligence which is most relevant to the German market. Our analysts are amongst the most experienced in their field and are always fully informed about current events.
We also keep you informed: On the DCSO CyTec Blog, you can find the latest information on the threat landscape and concrete analyses of attacks.
Tailored to the German economy
As a German company, we run our Security Operations Center (SOC) in Germany. You can therefore be sure that all data remains on site and is in the best hands as we comply with all data protection requirements for monitoring and analysing data streams and of course work in accordance with the DSGVO.
-
SOC operation in Berlin
-
Comprehensive data protection
-
Certified according to ISO 27001 and TISAX
-
Concentrated expertise

Whitepaper
Defending municipal utilities and local suppliers against cyber attacks
[contact-form-7 404 "Not Found"]
Whitepaper
Cyber security in mechanical engineering 2025 and beyond
[contact-form-7 404 "Not Found"]TDH COMPLETE
FAQ
Keep control over your
digital footprint
Sensitive company information and personal data are extremely valuable – and therefore become the focus of attackers. Far too often, valuable and sensitive data is either freely accessible or becomes available through a data leak, without the affected companies noticing. When in the wrong hands, this data becomes an imminent threat to your company.
Regain control over the digital footprint of your company and your employees with our two fully managed services:
Contact